How ITAM fights cyber threats at every stage of the IT lifecycle:
From research to retirement, IT asset management helps prevent security breaches at a foundational level.

Cybersecurity breaches pose sophisticated, ever-evolving threats to organizations of all shapes and sizes. In fact, in 2023, ransomware attackers received a record total monetary value of $1.1 billion. With how 2024 is trending, we’re on track to break that record again.
But when you’re hit by a cybersecurity breach, you’re not just hurt financially. You also risk permanent loss of reputation, trust, and customers.
What if there was a way to prevent security breaches as early as possible? What if you could bolster your cybersecurity posture across every stage of your IT lifecycle?
For both questions, the answer is IT asset management (ITAM).
It’s time to integrate cybersecurity into your ITAM program
ITAM helps you track, monitor, and manage your IT assets throughout their lifecycle, providing essential answers to questions such as:
- What IT assets do you own and where are they?
- What specifications do your assets have?
- Who uses them and what functions do they serve?
- How are they configured, updated, and tracked?
- How much do they cost and what value do they deliver?
- Do they comply with policies and regulations?
With this information, ITAM helps improve your cybersecurity with improved visibility and insights. To understand all the positive effects ITAM can have on your cybersecurity posture, let’s explore how you can incorporate security into every phase of your assets’ lifecycles.
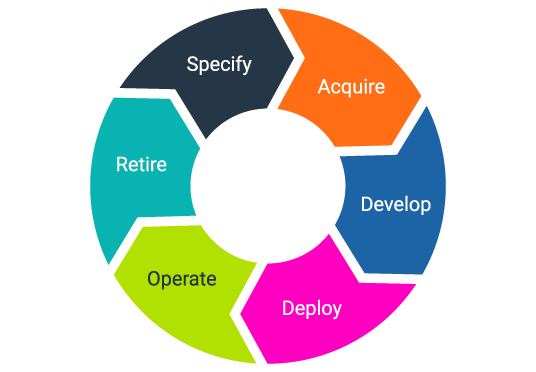
The IT asset lifecycle at a glance
Phase 1 of the ITAM lifecycle: Specify
Believe it or not, asset management starts before you’ve even made your purchase.
Prior to any acquisition is the specification phase of the IT asset lifecycle. During this phase, you must rigorously evaluate vendors and products, including assessing whether their security features meet your requirements and standards. This first phase of your ITAM program helps you select secure and compliant products, reducing the risk of introducing vulnerabilities into your IT environment.
For software, work with your InfoSec team to answer questions such as:
- Will the software be in the cloud, on-prem, or via SaaS?
- Are there any known vulnerabilities?
- Will the software integrate with your security tools and systems?
- Is it compatible with your OS and hardware specifications?
- Does it have the right update mechanisms in place?
- In compliance with GDPR, HIPAA, etc., can the software be discovered and managed? Is there an audit trail?
Phase 2: Acquire
Are you confident you’re buying your software and hardware from legitimate sources? To procure with confidence during the acquisition phase of your assets’ lifecycle, your ITAM program should:
- Ensure all software and hardware complies with relevant licensing and regulatory requirements.
- Verify all software has not been tampered with and comes from legitimate sources.
- Conduct risk assessments to identify potential security risks and implement appropriate mitigation strategies.
- Assess required levels of support and maintenance, as well as any EOL/EOS details.
- Manage vendor contracts, including terms related to security updates, patches, and support necessary for protecting against vulnerabilities and threats.
By embedding these practices into the acquisition phase, ITAM can further prevent new assets from introducing unnecessary risks while integrating into your IT environment.
Phase 3: Develop
In the develop phase, ITAM works with your operations teams to ensure all IT assets are configured securely before deployment.
This involves applying best practices for system hardening, such as:
- Disabling unnecessary services.
- Changing default passwords.
- Implementing strong access controls.
- Establishing the patch management process.
Phase 4: Deploy
ITAM ensures all deployment activities are well-documented for auditing and regulatory compliance. These detailed records also support transparency and accountability, which are critical for maintaining a secure environment.
When deploying IT assets, your ITAM program must ensure they:
- Adhere to your security policies, including encryption standards, password policies, network security measures, and more.
- Align with the versions, editions, and specifications defined in phase one.
- Allow for role-based access controls (as needed), ensuring only authorized personnel have access to specific assets and systems.
During and after deployment, your ITAM program should also record all hardware and software assets into a centralized inventory. This visibility is crucial for identifying and managing potential security risks as early as possible.
Phase 5: Operate
Once assets are deployed, your ITAM program can provide a holistic view of your hardware, software, networks, and the devices connected to them – including location, status, and configuration.
With this visibility, you can quickly act on unpatched or unsupported software, address known vulnerabilities, or identify missing assets. Here’s how:
- Identifying vulnerabilities, such as malware, missing patches, misconfigured settings, and outdated, rogue, or unauthorized software.
- Assessing the severity and impact of vulnerabilities so you can remediate them accordingly.
- Prioritizing assets by importance, sensitivity, and vulnerability so you can effectively allocate resources and efforts.
- Accelerating security alert responses to locate and isolate affected assets, identify the root cause and scope of incidents, and contain and resolve issues.
- Mitigating security risks by identifying and eliminating redundant, obsolete, and underused IT assets.
All the while, ITAM gives you deep insight into which roles need access to certain data and applications. This enforces least privilege access, giving users permission for only what’s required for their day-to-day.
Phase 6: Retire
Once assets are replaced or retired, it’s crucial to dispose of them securely – because even unused assets can pose a risk to cybersecurity. Proper decommissioning bolsters your security in a variety of ways, including:
Data erasure and sanitization:
Secure data wiping completely erases data from devices before disposal or recycling. This can involve using data destruction software to overwrite data multiple times. To render critical, highly sensitive data unrecoverable, physical destruction (e.g., shredding hard drives) is also an option.
Compliance and regulatory requirements:
Adhering to industry standards and legal requirements (e.g., GDPR, HIPAA) helps avoid data breaches and legal penalties by establishing best practices for data destruction, including maintaining documentation and certification of data destruction activities from third-party vendors.
Policy enforcement:
Establish and enforce retirement policies and procedures for your assets. In doing so, you can ensure siloed personnel, smaller teams, and tertiary locations follow the same rigorous guidelines as your broader organization while preventing any data from slipping through the cracks.
Recycling and repurposing:
Secure repurposing ensures assets are wiped and reconfigured before they’re reissued or resold, preventing unauthorized access to data. If assets are being decommissioned, follow environmentally friendly practices to prevent the destructive disposal of e-waste and allow for components and precious metals to be recycled for future manufacturing.
Dive deeper into ITAM’s many cybersecurity benefits with our interactive infographic: The importance of IT asset management (ITAM) in cybersecurity.
Your next step: Refine your ITAM strategy
Whether you’re just starting to consider ITAM for your organization of you’ve already begun the research process, you can gain the best understanding of your current state by reviewing your overall ITAM and cybersecurity strategies.
ITAM experts, including SHI’s own lifecycle management specialists, have years of experience tailoring asset management tools and capabilities to the unique use cases of organizations big and small.
Our expertise extends not just to asset management, but to cybersecurity as well – ensuring the solutions you select help reduce security gaps and protect your data, users, and equipment.
SHI’s ITAM process consulting services analyze your ITAM processes, identify gaps and shortcomings, and uncover solutions to your most pressing (and sometimes hidden) issues and vulnerabilities. For many organizations, ITAM process consulting is an important first step for bringing their IT asset management into the modern era.
Are you ready to boost your cybersecurity with IT asset management? Contact SHI to engage our ITAM process consulting services.




