Cybersecurity and privacy in the wake of GDPR
It’s important to understand what you’re facing and focus your efforts on three key areas

Organizations that collect, use, and share personal information are facing a sea change in the legal landscape for data protection and privacy. A wave of new consumer privacy regulations have followed in the wake of the General Data Protection Regulation (GDPR), forcing U.S. companies to comply with multiple state-based rules.
As of March 2018, all 50 states have enacted breach notification laws that require businesses to notify consumers when their personal information has been compromised; in some cases, within 72 hours.
Additionally, several states have passed laws that provide GDPR-like consumer rights.
To successfully ride this wave of consumer privacy laws, it’s important to understand what you’re facing and focus your efforts on three key areas that can enable you not only to achieve compliance, but to truly protect your data.
California game-changer
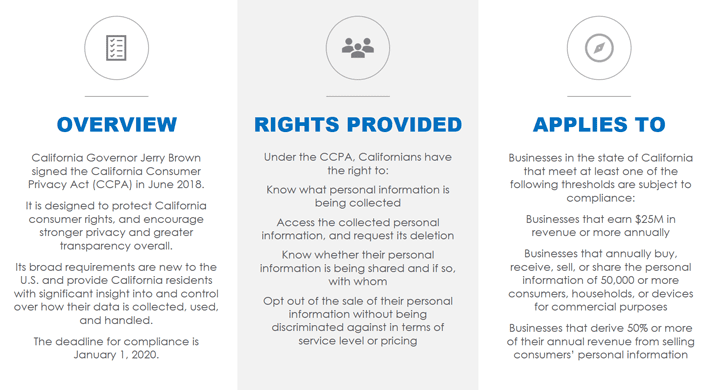
The California Consumer Privacy Act (CCPA) — passed last summer in response to the Facebook-Cambridge Analytica scandal — is set to become the most sweeping data privacy law in the U.S. The act goes into effect on January 1, 2020, and provides similar protections to those within the GDPR, including the “Right to Know,” “Right to Access,” “Right to Opt-Out,” and “Right to Deletion.”
Businesses that violate the CCPA will be subject to penalties of up to $2,500 for each unintentional violation, and $7,500 for each intentional violation. It is important to note that each user’s profile represents an independent violation.
To put that into perspective, consider the fines Facebook could have faced had it been found in violation through the Cambridge Analytica scandal. With an estimated 24.6 million Facebook users in California, the company would be staring at a maximum penalty of over $61 billion for an unintentional violation affecting all users, and $184 billion for an intentional violation if the CCPA had been in effect.
Jumping on the bandwagon
Eleven other U.S. laws designed to give consumers greater control over their data have recently been passed as well. Some simply expand data breach notification rules. Others, such as those in Colorado and Vermont, require companies to make substantial changes to the way they process data.
Additional states — including Maryland, New Jersey, and Washington — have similar legislation pending that includes their own unique version of rights, requirements, and penalties.
If you are unsure which of these regulations apply to your organization, you may need to engage the services of privacy consultants, and/or experienced privacy- and technology-focused lawyers.
Roadmap to readiness
Complying with a patchwork of regulations that have overlapping and sometimes conflicting requirements presents significant challenges. The CCPA deadline is less than seven months away; while 72% of organizations in a recent survey said they plan to invest in technology tools and 71% said they expect to spend more than six figures to assist with compliance efforts, the vast majority have a long way to go.
Only 14% of companies are compliant with CCPA, and 44% have not yet started the implementation process. Of companies that have worked on GDPR compliance, 21% are compliant with CCPA, compared to only 6% of companies that did not work on GDPR. – TrustArc
Three keys to success
Whether your organization is preparing for the CCPA or other data protection and privacy regulations, focus your efforts on discovering and identifying regulated data, and then managing and protecting it. You can meet many requirements through the implementation or advancement of data-centric security, incident response, and third-party risk management programs.
Data-centric security
Instead of trying to protect everything, focus on protecting what matters most — sensitive and regulated data. With data-centric security you can achieve:
- Visibility into where sensitive data is located, how it flows within your organization, and where it’s at risk
- Classification of sensitive data
- Monitoring and controlling access to and use (or misuse) of data
Key data-centric security technologies include data discovery, data classification, data loss prevention (DLP), identity and access management (IAM), data governance, cloud access security brokers (CASBs), and encryption. Both the GDPR and the CCPA call for encryption; when compromised data is encrypted, companies have protection against unauthorized access and reduced liability.
Incident response
Accept that you’re going to experience security incidents regularly, and be ready to respond. State breach notification laws are in force across the U.S., and strict 72-hour notification mandates within the GDPR, the New York State Cybersecurity Requirements for Financial Services Companies, and the South Carolina Insurance Data Security Act require organizations unaccustomed to responding to incidents within strict timelines to mature their capabilities.
Having a complete, up-to-date incidence response plan in place is critical. Many organizations rely on incident response frameworks such as NIST 800-61 and ISO/IEC 270035 for guidance. Professional services such as security program assessments can also help. With the right team, tools, and strategic partnerships in place, you can comply with requirements and extend your capabilities to minimize damage and protect against future intrusions.
Third-party risk management
Address third-party risks. It’s common for service providers and other partners to have access to internal systems, making them attractive stepping stones to hackers’ true target — your data.
23% of organizations with 5,000+ employees say they have more than 500 vendors logging in regularly, and 58% believe it’s likely they have experienced a breach from compromised vendor access. – BeyondTrust Privileged Access Threat Report 2019
Third-party weaknesses are your weaknesses, so make sure your partners and vendors are taking cybersecurity seriously. Carefully monitor their security practices — engaging in third-party due diligence and periodic assessments — to ensure that requirements have been met throughout your supply chain.
Staying afloat
As personal data collection continues to expand amid growing cyber threats, so will the wave of privacy legislation. Regulators around the world are telling us they mean business, and every organization that collects, stores, and uses sensitive customer data needs to heed the wake-up call and raise the bar on their cybersecurity practices to stay afloat.
By maturing your organization’s capabilities with comprehensive data-centric security, incident response, and third-party risk management programs, you can enhance your brand reputation, win consumer trust, and gain the agility you need to keep up with the threat landscape.
Contact your SHI account executive to learn more about maturing your security posture.
Anne Grahn contributed to this post.