How brushing up on your IAM health and hygiene keeps breaches at bay:
Maintaining healthy IAM protocols isn’t just best practice — it’s a frontline defense against costly data breaches.

You’ve probably heard the saying: “You don’t have to brush all your teeth — just the ones you want to keep.” The same principle applies to identity and access management (IAM). For both, regular hygiene prevents expensive and painful problems down the road.
Like other health-related habits, neglect over time creates real problems. And while your organization may not experience a breach today, failing to prioritize IAM hygiene increases the potential for attackers to leverage new threat vectors and compromise your network.
Consider a recent advisory from the U.S. Cybersecurity and Infrastructure Security Agency (CISA). It made headlines not because investigators found a breach, but because they didn’t.
2025 CISA advisory shares hygiene failures as serious as attacks
This summer, CISA and the U.S. Coast Guard (USCG) issued advisory AA23-212A following a proactive threat hunt within a critical infrastructure organization.
The advisory outlined that although there was no evidence of malicious activity, they found serious IAM hygiene issues, including insufficient logging, insecurely stored credentials, and shared administrator accounts.
As a result, CISA urged organizations to “review and implement the mitigations listed in this advisory to prevent potential compromises and better protect our national infrastructure.”
The takeaway? When it comes to IAM health and hygiene, no breach does not mean no risk.
Why do organizations struggle with IAM hygiene?
So why do organizations still struggle with the very practices that prevent cybercriminals from turning identity gaps into a payday? In short, it’s because IAM is complex, often fragmented across teams and tools, and difficult to measure and mature without a clear roadmap.
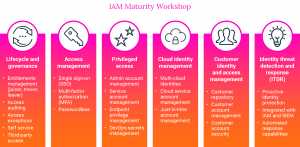
That’s where the SHI IAM Maturity Workshop comes in. It is a two to three-hour deep dive with all relevant stakeholders, ensuring no gaps are missed, and every voice is heard. It addresses these challenges by providing:
- A comprehensive view across six IAM pillars that provide the structure and clarity to assess your IAM program.
- A proprietary maturity matrix that gives you a clear score across the six pillars and an actionable roadmap for improvement.
- Prescriptive recommendations for each pillar, including specific steps, product suggestions, process improvements, and tool consolidation strategies.
- Hands-on support with ongoing guidance, lab demos, and follow-up meetings to help you implement recommendations and achieve lasting improvements.
Today’s top eight IAM challenges — and how our IAM Maturity Workshop addresses them
Through years of collaborating with cybersecurity teams, we’ve identified eight major IAM challenges teams face today. Here’s how our IAM Maturity Workshop helps you solve them.
1. Reliance on manual processes
Why this matters:
Manual workflows slow response times and increase human error. These inefficiencies often lead to excessive permissions — accounting for 31% of identity-related breaches.
How our IAM Maturity Workshop can help:
Lifecycle and governance make up the first pillar of our workshop. Here, we assess how you manage entitlements today, then make recommendations to introduce automated processes that can help you mature your IAM posture for both short-term gains and long-term resilience.
2. Lack of unified visibility
Why this matters:
Without unified visibility, blind spots can multiply — especially in hybrid and multi-cloud environments, making it harder to detect IAM gaps before attackers do.
How our IAM Maturity Workshop can help:
Our workshop starts with a focused, two-hour discovery session to map out your IAM landscape. We identify what you can see — and what you can’t — so you get a complete picture and steps to close visibility gaps.
3. Fragmented identity ownership and infrastructure complexity
On average, identities are stored within 4.8 systems, while 94% of cybersecurity leaders say complexity in identity infrastructure challenges security posture.
Why this matters:
Multiple teams managing IAM create gaps and overlaps, while dispersed identity data makes enforcing consistent policies especially difficult.
How our IAM Maturity Workshop can help:
Our workshop brings all identity stakeholders together to examine IAM holistically. After fostering alignment and collaboration, we provide recommendations to streamline complexity without sacrificing security.
4. Tool sprawl and integration gaps
Why this matters:
Disconnected tools add complexity and costs. When systems don’t communicate, security teams waste effort chasing alerts across silos, while attackers plan their next move.
How our IAM Maturity Workshop can help:
Our experts assess where your IAM environment is over-or under-protected across your tools and recommend strategies to consolidate tools where appropriate, streamline operations, and strengthen security posture.
5. Unevenly applied identity controls
27% of identity breaches stem from inconsistent access controls across cloud environments.
Why this matters:
Non-uniform policies create weak links, turning minor misconfigurations into major risks.
How our IAM Maturity Workshop can help:
We assess how consistently your identity policies are applied across environments, pinpoint enforcement gaps, and provide practical steps to standardize controls — reducing risk without slowing down operations.
6. Unmanaged endpoints and expanding attack surface
Why this matters:
Hybrid work and BYOD dramatically expand the identity attack surface. What feels like convenience for employees often creates unmanaged endpoints for your security team, which are prime entry points for attackers.
How our IAM Maturity Workshop can help:
We assess your endpoint and device access controls as a part of the lifecycle and governance pillar, identify unmanaged identities, and recommend hygiene standards. Our practical steps for continuous monitoring and policy enforcement reduce risk without slowing the workforce’s productivity.
7. Repeated failed audits and uncertainty about next steps
Why this matters:
Knowing what’s wrong in your IAM landscape is only half the battle. Without a clear roadmap for remediation, organizations remain stuck in a cycle of repeated audit failures and growing risk exposure.
How our IAM Maturity Workshop can help:
We help you prioritize your cybersecurity investments for maximum risk reduction. Our workshop not only guides you toward audit compliance but also benchmarks your IAM maturity across six foundational pillars, so you know where there’s still room to grow.
8. AI amplifying existing IAM gaps
68% of respondents lack identity security controls for AI and LLMS.
Why this matters:
Identity-based attacks rose by 32% in the first half of 2025. Experts suggest this surge reflects adversaries using AI, though it’s important to distinguish that AI attacks don’t create new vulnerabilities; they accelerate the exploitation of the gaps you already have.
How our IAM Maturity Workshop can help:
We help you close your IAM gaps overall — standardizing policies, strengthening controls, and reducing your attack surface — so even AI-powered threats have fewer opportunities to succeed.
Going from gaps to gains with our IAM Maturity Workshop
Throughout this article, we’ve explored eight common IAM hygiene challenges. Like plaque buildup, these issues accumulate silently and create weak spots that become major problems down the road. The good news? Whether it’s dental care or cyber defense, disciplined hygiene and the right partnerships can turn weaknesses into wins.
What makes the SHI IAM Maturity Workshop different?
- Integrates improvements across six pillars — because real security strengthens when everything works in tandem.
- Delivers executive-ready insights about your IAM landscape to help you secure buy-in and guide investment decisions.
- Educates your team on best practices, toolsets, and methodologies — especially critical after a failed audit.
- Provides a tailored maturity roadmap that moves you from a crawl to a walk to a run (where appropriate), with practical steps that deliver measurable progress.
Just like brushing your teeth, IAM hygiene isn’t glamorous — but it’s essential. When IAM hygiene becomes a habit in your organization, you build the foundation to outsmart threats and solve what’s next.
Looking for more IAM strategy and insights? Download our latest ebook, The modern IAM playbook, for practical guidance on building a unified identity approach across the six IAM pillars.
NEXT STEPS
Ready to turn IAM from a vulnerability into a strength? Read more about our IAM workshop and start brushing up on your IAM hygiene with one of our cybersecurity experts today.