Want to integrate effective DevOps security? Our experts explain how:
Gain expert insight into how you can start your DevSecOps journey on the right foot.

If DevOps is about the speed of delivery for your development pipeline, then integrating security practices will just slow you down – right? After all, adding extra measures to secure your code sounds a lot like adding speed bumps to Main Street. People will drive safer but take longer to reach the end of the road.
Luckily for you, slowing down DevOps in the name of security doesn’t have to be the norm. With the right processes in place, DevSecOps helps you have your cake and eat it too by ensuring you can deliver secure code while still meeting your deadlines.
We spoke with SHI’s resident DevOps experts to explain how this is possible, and what you can do to start efficiently securing your DevOps pipeline.
Don’t let misconceptions drag you down
 “The easiest way to avoid a DevSecOps slowdown? Bring in your security team early and often,” says Christina Halikiopoulos.
“The easiest way to avoid a DevSecOps slowdown? Bring in your security team early and often,” says Christina Halikiopoulos.
Christina is a Security Solutions Engineer at SHI. She has a penchant for helping customers enact best secure coding practices and effective security strategies. To Christina, the inherent slowdown most people associate with DevSecOps is just a common misconception.
“Security and app development teams aren’t enemies. They should function as one cohesive team from the onset.”
It’s happened all too often – your development team has worked six months building millions of lines of code. After all that time and effort, you test or release your product, only to find overlooked and implicative security flaws. You have no option but to send it back and start patching or, worst case scenario, restart the entire process.
“It’s a huge time and cost sink. After all that time, the developers who originally built that code may not even be in those roles anymore. Bringing your security team into the process early is how you avoid that nightmare scenario. You won’t need to throw any wrenches into your development because security will be built into the code from day one.”

Alongside Christina, we also spoke with Clinton Davenport and Brad Bowers. As a Cloud Solutions Architect at SHI, Clinton has over two decades of experience building resilient, world-class user experiences.
“I explain it to customers like this,” Clinton says. “Looping in security does slow you down initially, but it actually speeds you up in the long run. As soon as your teams get past the learning curve of how to work together, continuous compliance feedback can happen in the development process instead of after the rollout – minimizing roadblocks and reiteration. Your teams will also minimize wasted time with the feedback loop for security baselines being communicated automatically. Development and security will be in lockstep. In essence, you need to slow down, then speed up.”
It’s time for DevOps to shift left
SHI’s Field CISO, Brad Bowers, says inefficient workflows are a huge reason why so many organizations mistakenly see security as a stumbling block to their development practices.
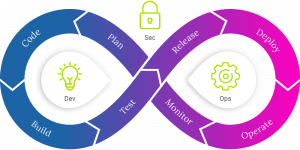
“By shifting left,” Brad says, referencing the DevOps infinity loop, “you can incorporate security without impeding your development cycle.”
To shift left, your organization must refocus security testing and quality assurance early in the development phase of your DevOps cycle – when you plan, code, and build applications. By doing so, your teams can identify vulnerabilities, risks, and improvements early enough to avoid undo setbacks.
“You may have the right tools,” Brad continues, “but it’s about pairing them with the right workflows and policies. Shifting left? That’s golden.”
What are practical ways to secure your DevOps?
DevSecOps is more than a technological change; it’s primarily a cultural one. That means fostering an atmosphere where your developers have a say in the security tools they use – and where they aren’t cutting corners to deploy a minimum viable product.
“Make it as easy as you can for developers to use the security tools at their disposal,” Christina says. “The intent is for them to use these tools effectively on every application. If you or your security teams force developers to leverage tools they’re unfamiliar or adverse to, you’re not going to see the consistent use you need.”

“Most development shops, especially large ones, are under intense pressure to output code,” says Brad. “The culture of a ‘minimum viable product’ still permeates through a lot of development houses. When securing your DevOps, think of how tools and workflows can be streamlined to help developers finish code in a timely manner while still being secure.”
According to Clinton, cultural change starts from the top down. “DevSecOps can’t be a grassroots effort. It can’t be a lone group or in one silo. Think about your biggest security champions, your agents of change, and work with them to map out your strategic vision. Show unity amongst leadership and set DevSecOps as an organization-wide priority.”
Avoid paralysis by analysis
Setting priorities across your entire organization doesn’t mean you should try boiling the ocean. In fact, you should be doing the opposite – start out small, then scale your strategy out once you find success.
“It’s paralysis by analysis,” Clinton says. “Don’t try to do everything once. Take one specific app stack, one specific team, and add the security gates needed to build up their resiliency. Develop your strategy for the long term, make adjustments as needed, then scale out in smaller, more tactical bites.”
Protect your application’s perimeter
As software becomes ready for testing or deployment, you need to ensure every component is protected from tampering and unauthorized access. For Christina, Clinton, and Brad, this means:
- Securing your development environment and endpoints
- Having mature practices for code repositories and supporting artifacts
- Providing repeatable mechanisms for verifying software integrity
- Implementing least privilege access
“You don’t want malicious actors getting their hands on your source code,” Christina says. “With a web application firewall (WAF), you can log and monitor activity so you can maintain complete visibility and control over who has access and how secrets are managed.”
Be aware of API and open-source code risks
So many organizations consume or rely on APIs and open-source code, yet few have a firm understanding of how they were coded, maintained, or validated from a security perspective. For Brad, the answer largely lies in knowing the provenance and lineage of your code.
As an example, “You’re leveraging an API from a partner. Where does the source code in that API really come from? What’s its provenance? How is the code managed, validated, and secured? That API may leverage numerous open-source modules that are supported by various ‘unknown’ third parties.”
Brad adds that learning the provenance of source code is a key step to understanding where risks or vulnerabilities may reside in the APIs and open-source code used in your applications.
How can you start your DevSecOps journey?
Whether you’re starting your DevSecOps journey from scratch or need to double back from trying to boil the whole ocean at once, the first few steps of creating an effective DevSecOps strategy are often the most difficult. But if you take a step back and simultaneously start small and think long-term, you can create an actionable plan that can scale organization-wide.
Step one: Designate your security champion
Your security champion will be someone who understands the ins and out of application development and will work with both sides of the DevSecOps spectrum to achieve team and stakeholder buy-in, as well as define the tools your developers need to securely and efficiently output code.
“When identifying your security champion, look for someone who can speak to the ways your organization secures not just your applications, but also your users, data, network – your entire organization. Your champion needs to consider all of that, while also understanding the tools your developers use on a daily basis,” Christina says.
Identifying a security champion can be tricky. It’s hard for most people to remove their roles’ blinders and take a holistic look at the task at hand. That’s where trusted guidance can help.
“Through our assessments and workshops, SHI has the resources to help you better understand your organization’s environment. We provide the clarity you need to form that broader perspective of what tools and processes are needed to achieve your DevSecOps goals,” says Christina. “To Clinton’s earlier point, it’s about helping you start small and think long-term.”
Step two: Perform application security testing
Once you’ve identified your security champion, pick your first application stack and perform app security tests. These tests help you spot vulnerabilities and flaws in your coding, as well as evaluate your logging and monitoring tools.
“These tests go beyond just security,” Christina says. “Through things like lab trainings, they teach developers what secure coding actually looks like, in a way that’s fun and engaging for them. These security tests are so much more fruitful than, say, having your developers stare at a bunch of videos.”
Step three: Identify the best security model for your use case
While your DevSecOps strategy may be in its infant stages, you’ve likely built some form of security practice for your broader organization – or you’re already leveraging a well-known framework, such as NIST 800-218. But as you seek to define the DevSecOps tools you need to succeed, it can be difficult to parse between what’s recommended in most cases, and what’s best for your case.
“These models tell you what you should or can be doing, but often leave you wondering how you can do it,” Brad says. “You write x type of code in y environment using z tools. Which models fit your use case? What control should you align with? SHI can help find the best-fit solutions for your needs.”
To identify the right model for your organization, SHI helps you:
- Assess your current technologies and the tools you’re missing
- Create a roadmap for adopting missing tools and bolstering maturity
- Align disparate tools with your long-term business goals
As is the case with identifying a security champion, it’s hard to make these decisions without blinders narrowing your vision. According to Clinton, “More often than not, IT security and development teams don’t consider the business perspective, because that’s typically outside their roles. But that’s where it all starts. There needs to be a business justification to the time and money you’re spending adopting these solutions.”
That’s why we recommend starting your DevSecOps journey from the top down. You can build alignment across your leadership, making it easier for stakeholders to unite behind the time or resources you may need to spend developing your ideal strategy.
Solve what’s next at SHI’s cybersecurity roadshow
This April, Christina, Clinton, and Brad will feature in SHI’s cybersecurity roadshows, where the expert trio will share deeper insight into how your organization can best integrate security into your DevOps. You’ll learn how to:
- Shift left and shield right
- Overcome culture and workflow roadblocks
- Address the challenges of introducing DevSecOps into siloed teams
As we concluded our interview with Christina, Clinton, and Brad, we asked them what they hoped your takeaway would be during our cybersecurity roadshow. The sentiment was unanimous: our experts want to help you gain the confidence you need to get started on the right foot.
“Everyone struggles with this new standard,” Clinton says, “but I hope our sessions will help you feel confident enough to drive the conversation within your organization.”
Christina adds, “I hope you’ll see DevSecOps’ downstream affects – your customers will have more confidence in you, knowing your application and, in turn, their data is secure. DevSecOps isn’t a one-time purchase, it’s a journey. It’s an ongoing effort to protect your organization – from your applications and data to your reputation.”
“Organizations interested in DevSecOps no doubt have questions,” Brad says. “I hope we’ll have answered yours during our roadshow. But more importantly, I hope you walk away knowing you can come to us with any of your questions, and you can trust us to give honest, independent answers, with resources to set you on the right path toward achieving your goals.”
To attend our upcoming cybersecurity roadshow and gain more DevSecOps insight from Christina, Clinton, and Brad, reserve your spot today




