Demystifying FIDO and the path to passwordless authentication
It’s time to consider reducing your dependence on passwords

Passwords are a critical cybersecurity problem.
They are hard to remember. They are easy to break. They are often reused. And the increasing sophistication of spear-phishing campaigns makes them easy to steal.
More than 80% of hacking-related data breaches involve compromised credentials. Bill Gates predicted the demise of password-based security more than a decade ago, asserting that it cannot “meet the challenge” of protecting critical information.
In an effort to reduce the reliance on passwords, the Fast IDentity Online (FIDO) Alliance was launched in 2012. Backed by organizations such as Amazon, Intel, PayPal, Lenovo, Visa, Google, Microsoft, Samsung, and Apple, it’s an open industry association with a mission to enable simpler and stronger user authentication.
What FIDO does
FIDO overhauls the login process by standardizing the use of hardware devices such as security keys for authentication. Whereas multi-factor authentication (MFA) grants access based on the presentation of evidence within three categories – something you know (e.g., a password), something you have (e.g., a software or hardware token), and something you are (e.g., biometrics) – FIDO seeks to eliminate the vulnerable knowledge factor.
FIDO standards – UAF, U2F, and FIDO2 – are designed to protect user privacy and support nearly any type of authentication, including biometrics, one-time passwords (OTP), trusted platform modules (TPM), USB security tokens, near-field communication (NFC), and Bluetooth for mobile devices.
The standards provide a framework for removing common attacks against passwords such as credential stuffing, password reuse, phishing, and man-in-the-middle (MITM) attacks. The most recent, FIDO2, enables passwordless authentication based on public key cryptography.
FIDO2 specifications include WebAuthn and Client to Authenticator Protocol (CTAP). WebAuthn makes hacking harder by enabling online services to use FIDO Authentication through a standard web API that can be built into browsers and related web platform infrastructure. It is currently supported in Google Chrome, Mozilla Firefox, Microsoft Edge, and Apple Safari, as well as Windows 10 and Android platforms.
CTAP enables an external authenticator – such as a physical FIDO security key or a mobile phone – to work with browsers that support WebAuthn for easy authentication to online services.
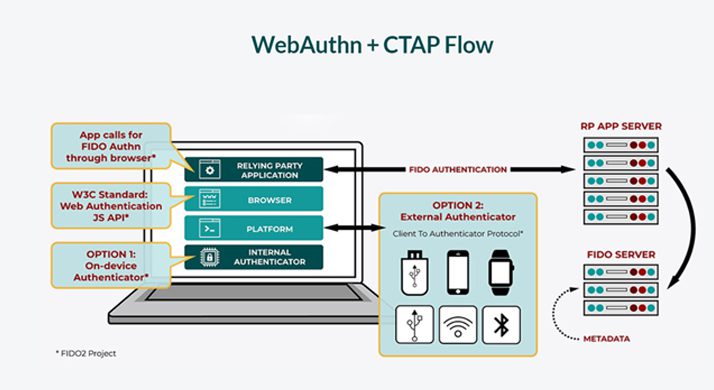
Image source: FIDO Alliance
How FIDO works
Stronger authentication is provided through cryptographic login credentials that are unique across every website, never leave the user’s device, and are never stored on a server.
During registration with an online service, the user’s device (or authenticator) creates a public key and private key. It retains the private key and registers the public key with the online service. Authentication is accomplished when the user proves possession of the private key to the service by using it to respond to a challenge. The private key can be used only after the user unlocks it locally on the device. They can do this by scanning a fingerprint, speaking into a microphone, inserting a second-factor device, or pressing a button.
This approach – authenticating locally but using another protocol to securely communicate to the “relying party” (the host, application, or website requiring authentication) – enables organizations to move away from vulnerable credential stores and eliminate phishing.
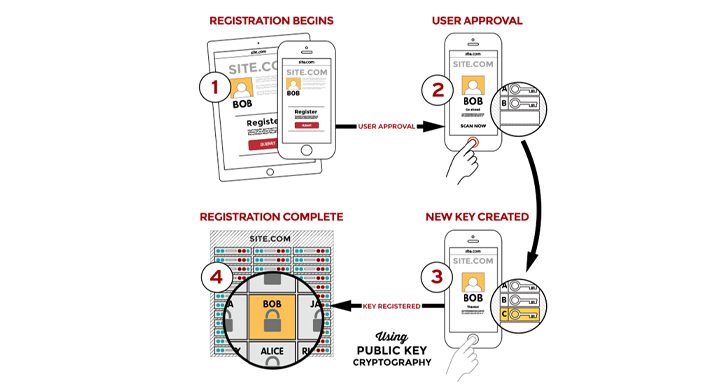
Image source: FIDO Alliance
Gaining momentum
While FIDO authentication is viewed by many security experts as a game-changer, it’s been slow to catch on.
Passwords are easy and familiar. Many organizations aren’t ready to take on the burden of replacing passwords with security keys that need to be set up and registered. Leading identity and access management technology providers report only a small percentage of enterprise customers actively pursuing FIDO authentication strategies.
However, evolving threats and data privacy regulations are stirring up interest in the standards. According to a recent study, 70% of businesses are facing strong regulatory pressure to provide better authentication for their customers.
Now that Apple has joined the alliance, all major platform providers and an increasing number of security vendors are firmly behind FIDO. Additionally, the recommendation of WebAuthn as an official standard by the World Wide Web Consortium (W3C) has paved the way for greater use of browser-based authentication (versus solely mobile, as in previous standards).
FIDO’s certification programs are creating an interoperable ecosystem of products and services that can be leveraged to deploy FIDO Authentication. Over 688 products have already been certified, ranging from consumer brands to biometrics vendors and enterprises, including Google Android, Microsoft Windows Hello, Ping Identity, Symantec, RSA, and Yubico.
Now that the tools required to become less dependent on password-based security are in place, organizations should weigh the challenges associated with implementing FIDO against the risks presented by passwords.
Best practices for success
To effectively take advantage of FIDO standards and the authentication benefits they provide, consider the following best practices:
-
Get stakeholder buy-in.
Involvement at the IT, security, and business unit levels is critical to getting the time and resources required to incorporate new standards. Documenting the expenses and inefficiencies related to password resets and account lockouts — like the number of IT support calls fielded — can help you gain support.
-
Evaluate solutions.
FIDO is vendor-independent, and there are hundreds of products certified to interoperate with each other. Organizations need to choose from a wide range of form factors from different vendors offering various usability, availability, and security features. Vendor-independent technology partners can help you identify the right solutions for your needs by testing and evaluating the security of potential authenticators, and ensuring proper integration with existing security controls.
-
Start with high-impact use cases.
These include secure access to the following resources:
-
- Web-based applications, including SaaS applications
- Enterprise applications and technologies
- Operating systems and Active Directory domain-based accounts
- Cloud accounts and services supported by AWS, Azure, and Google
- Social media accounts
Start small and look for areas that can make the most impact on your organization, such as privileged users and critical applications.
Next-generation authentication
Passwords aren’t going anywhere just yet, but it’s time to consider reducing your dependence on them.
Security incidents, cyber threats, and regulatory pressures are rising, while the costs associated with implementing strong authentication have gone down. The standards-based, cryptographically backed approach offered by FIDO provides simple yet strong security that can usher in the next generation of authentication. In doing so, it can help us relieve the burden of passwords and protect critical systems and data.
Anne Grahn contributed to this post.





