How to improve threat detection and response with MITRE ATT&CK:
A compelling way to move toward a more threat-informed defense

Nine hours.
That’s the average time it takes a cyberattack to go from initially compromising a network to lateral movement, according to a recent threat report. Detecting and responding to intrusions before that clock runs out isn’t easy.
Security analysts spend countless hours sifting through alerts — essentially searching for a needle in a haystack — to identify threats, while deployment and maintenance issues often allow malicious activity to slip through unnoticed. In fact, the reality is that attackers infiltrate the majority of environments without being detected.
To enable more effective threat detection and response, organizations must incorporate threat intelligence and threat detection frameworks that look beyond simple indicators of compromise (IOCs).
The MITRE ATT&CK framework provides a compelling way to move toward a more threat-informed defense.
What is ATT&CK?
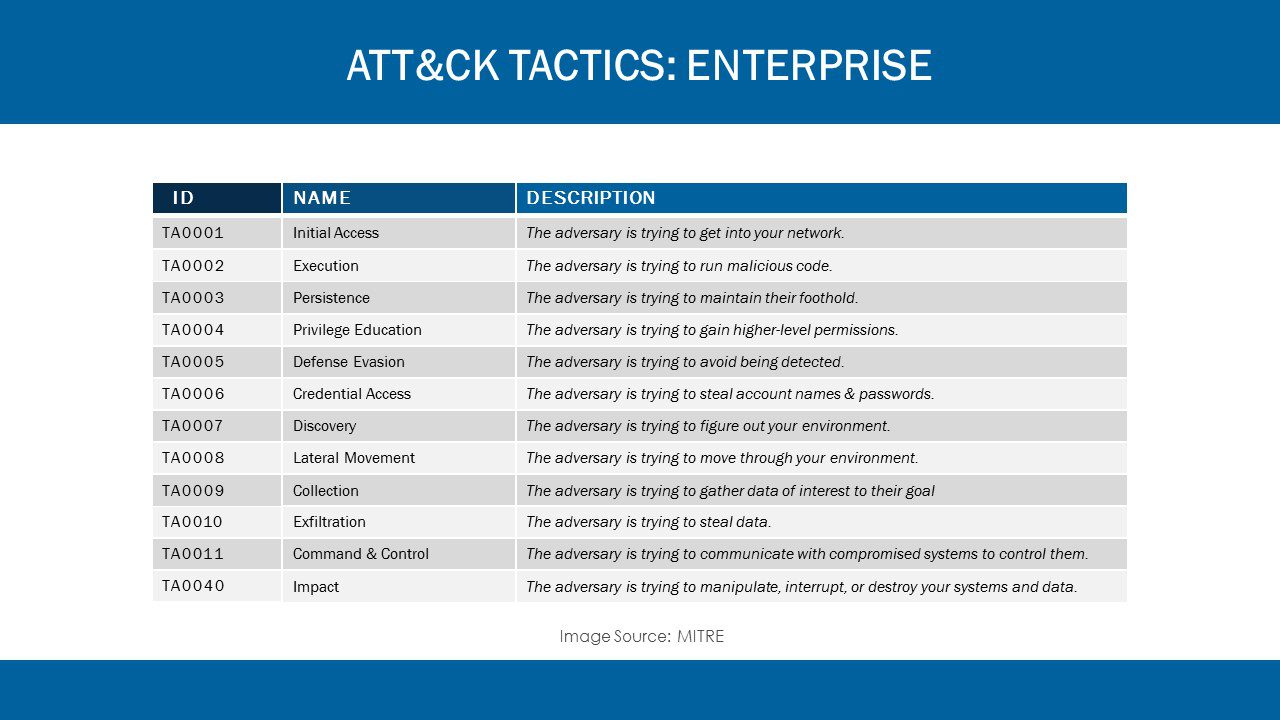
ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge. It is a free and globally accessible knowledge base created by MITRE in 2013 that documents and indexes attacker tactics and techniques based on real-world observations.
Information is displayed in matrices arranged by 12 tactics covering initial access through command and control, as well as the impact on the organization. This makes it easier for security teams to understand how threat actors might target their systems and data.
ATT&CK helps organizations identify and combat common intrusion strategies, commonly referred to as the “attackers’ playbook.”
When adversaries plan to infiltrate networks and exfiltrate data, they use multiple behaviors in different phases of the attack. Each phase consists of tactics (the “why” of the attack) supported by a set of techniques (the “how”), which use varying sets of procedures.
The initial tactic to gain a foothold in your environment is connected to one or more techniques, followed by another tactic with its techniques, and so on until the adversary has either reached their objective or been stopped. This layering of tactics down to specific procedures is where the acronym TTP comes from — tactics, techniques, and procedures.
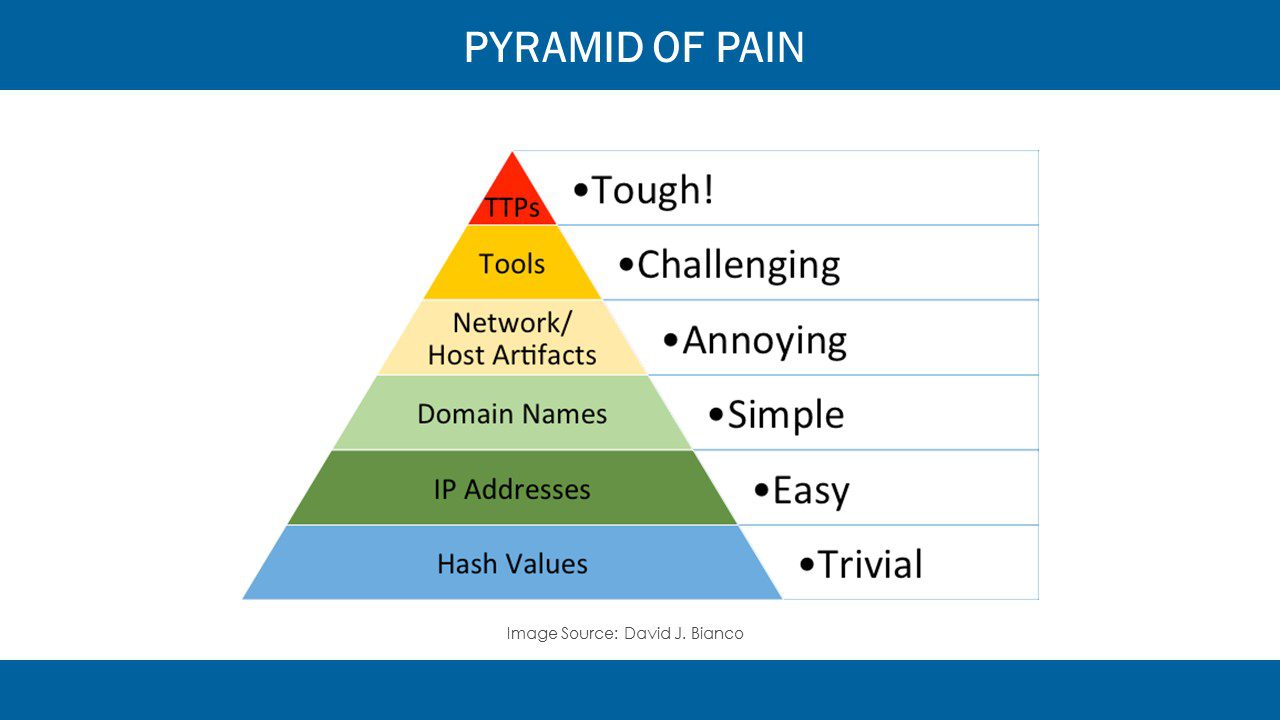
Summiting the pyramid of pain
In David Bianco’s “Pyramid of Pain” (pictured below), each level represents a different attack indicator that can be used to detect malicious activity, along with the correlating pain you will cause the attacker if you can successfully defend against that level of attack indicator. The higher up the pyramid, the more impact our efforts have.
ATT&CK is geared toward enabling detection and response at the apex of the pyramid. If you can detect and respond to behavior as opposed to basic indicators like suspicious file hashes or IP addresses, it becomes costly, time consuming, and difficult for the attack to continue.
The attackers would need to abandon the “playbook” and tailor their approach to your organization’s defenses — something most, with the exception of nation states, are either unable or unlikely to do.
Key use cases
ATT&CK provides a common vocabulary organizations can use to use to share information and build robust detection and response procedures.
There are four key use cases for security teams:
- Threat intelligence: Understand the attacks adversaries are using, and use that knowledge to anticipate and defend against threats.
- Detection and analytics: Use intelligence to build analytics and detect adversary behaviors.
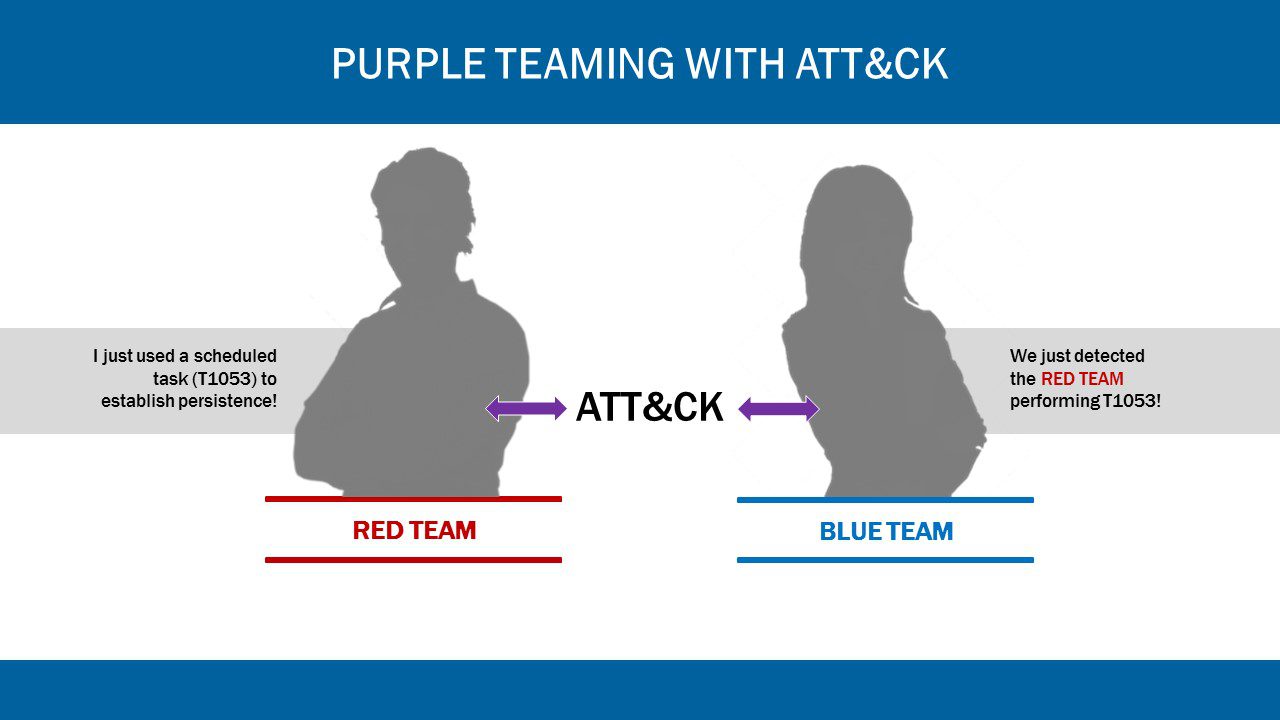
- Adversary emulation and purple teaming: Construct scenarios to test aspects of an adversary’s TTPs, and evaluate how defenses might fare against them. For instance, the Red Team develops a strategy to link together several techniques from different columns to test the defenses of their target. The Blue Team leverages the tactics and techniques to counter the Red Team’s strategy.
- Assessment and engineering: Evaluate how your current defenses stack up to techniques and adversaries in ATT&CK, identify gaps in coverage, and modify or acquire solutions.
Getting started
The MITRE ATT&CK framework is frequently updated with the latest discoveries of hackers and security researchers. The current version features 333 different techniques.
How can you focus on building detection and response mechanisms that will have the most impact on your efforts? Take the following actions:
- Know yourself: As Chinese military strategist Sun Tzu once said, “If you know the enemy and know yourself, you need not fear the result of a hundred battles.” Once you understand your organizational risks and identify your most valuable assets, you can target the techniques attackers are likely to use against you.
-
- Evaluate where your sensitive data resides, how it flows within the organization, and where it’s at risk.
- Determine the impact if critical business assets, data, IP, or systems were compromised.
- Identify what external attackers would target and why.
- Avoid analysis paralysis: Focus on identifying the techniques that are most relevant to your company’s sensitive data and systems.
- Consider levels of difficulty: Narrow down your list by aligning it with the skills of the team members you have available to build detections; use public resources to help you organize the ATT&CK matrix by difficulty of exploitation.
- Confirm the availability of data sources: If your organization doesn’t have data sources associated with a particular technique, writing a detection for it will be difficult. Look at the common data sources across different ATT&CK techniques in your environment, so you can maximize the number of detections you can create.
- Evaluate solutions that help you automate: Many leading security technology manufacturers provide integrations to the ATT&CK framework, enabling SOC teams to incorporate the intelligence into their workflows. Before choosing solutions, define your use cases for ATT&CK and preferred capabilities.
Many organizations leverage a vendor-independent technology partner to help them test and evaluate potential solutions. Professional security assessments can pave the way to successful deployment and integration by objectively detailing the current state of your security program and providing recommendations for leveraging ATT&CK to advance threat detection and response.
ATT&CKing cyber risk
Cyber attackers are not going to stop targeting you, and they’re constantly upping their game. According to Verizon’s 2020 Data Breach Investigations Report (DBIR), 70% of breaches over the past year were caused by outsiders, and 86% of cyberattacks were financially motivated.
While ATT&CK isn’t a silver bullet, and it does take work, applying it to your environment will help you detect intrusions and accelerate your response. By understanding your environment, gaining visibility into the TTPs attackers will likely use against you, and building the right solutions, you can start leveling the playing field.
Anne Grahn contributed to this post.