5 keys to successful privileged access management

Cybercriminals are targeting our most valuable systems and data, and privileged users offer the proverbial “keys to the kingdom.”
The abuse of privileged accounts can cause catastrophic damage to public and private sector organizations. An attacker who exploits privileged credentials can map IT infrastructure and jump from system to system, accessing and exfiltrating critical information.
Security teams are struggling to combat this threat both on-premises and in the cloud: A recent study found that 74% of data breaches involve access to privileged accounts.
The challenge for many organizations lies in identifying and protecting all their privileged accounts and account owners. Additionally, manually granting and revoking privileges is a time-consuming process. Projects to secure privileged access often fail to successfully implement least privilege, and omit groups with admin credentials such as help desk personnel or non-traditional social media accounts that can impact brand reputation.
But there’s good news. According to Gartner, by 2022, 90% of organizations will recognize that mitigation of privileged access risk is a fundamental security control, an increase from 70% today.
While privileged access management (PAM) is one of the most crucial aspects of effective cybersecurity, it requires a strategy that includes the right people, process, and technology.
Putting the right tools in place
Organizations are increasingly turning to PAM tools to help reduce risks associated with external attacks, insider threats, and third-party access. PAM technology exerts control over elevated (privileged) access and permissions for users, accounts, processes, and systems.
While PAM solutions help organizations automate the granting and revoking of privileged access, successful implementation depends on a careful approach that considers the following questions:
- Who (or what kind of user) is appropriate for each type of privileged access?
- What kind of access is appropriate?
- Where are the boundaries of the access?
- When is the access appropriate?
- Why is the access necessary?
5 keys to success
Five key elements can set you on the path to successfully securing privileged access.
1. Establish a solid privileged account discovery process. To eliminate unnecessary accounts and specify which accounts and users can access critical assets, you need to identify every use of privileged access, both on-premises and in the cloud. This includes traditional and non-traditional accounts used by people—including personal and shared accounts as well as administrative accounts such as local administrator and root—and by software. Because systems, applications, and accounts are constantly being updated, it’s important to establish a continuous process.
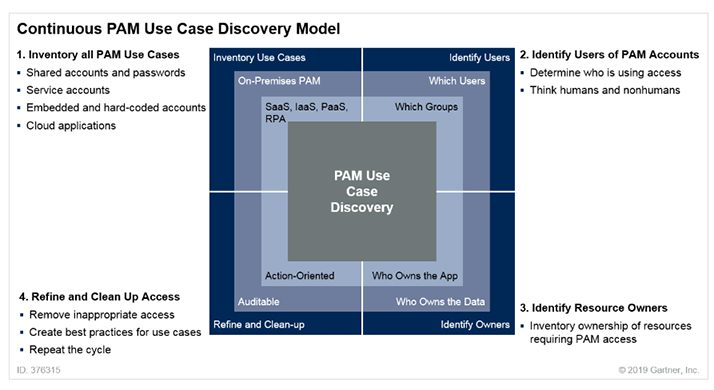
Image credit: Gartner
Discovery tools from PAM vendors should be integrated with additional controls. At a minimum, these include IT service management (ITSM), security information and event management (SIEM), identity governance and administration (IGA), authentication, DevOps tools, and ticketing systems.
2. Develop a privileged account password policy. It’s critical to create clear policies that everyone who uses and manages privileged accounts can understand and accept. Put in place a privileged account password protection policy that covers human and non-human accounts to prevent unauthorized access and demonstrate compliance with regulations.
You should use long passphrases–rather than seemingly complex passwords–and multi-factor authentication for human accounts. For non-human (services and applications) accounts, passwords should be changed frequently.
PAM controls automatically randomize, manage, and vault passwords, and enable you to update all privileged account passwords automatically and simultaneously.
3. Implement least privilege. To reduce the risk of attackers gaining access to critical systems or sensitive data, give users only the bare minimum privileges needed to do their jobs. Make sure you remove full local administrator access to endpoints.
Identity and access management (IAM) controls can help you grant least privilege access based on who’s requesting it, the context of the request, and the risk of the access environment without downtime or loss of productivity. When individual accounts require the ability to execute privileged tasks, PAM solutions can help you enable access that is confined to the scope and time required to complete the activity and remove that access afterward.
4. Choose the right solution. There are numerous PAM technology providers to choose from, with varying features and deployment options.
Before choosing, it’s important to define use cases for privileged access in your environment and preferred solution capabilities such as service account management, discovery functions, asset and vulnerability management, analytics, file integrity monitoring, SSH key management, and more.
Many organizations leverage a vendor-independent technology partner to help them test and evaluate potential solutions. Professional security assessments can pave the way to a successful deployment by identifying what your privileged accounts are protecting and objectively detailing current security policies, controls, and processes.
Organizations without the in-house staff needed to deploy, configure, and manage a PAM solution may want to consider a managed service provider (MSP).
5. Monitor accounts with analytics. Privileged accounts should be monitored continuously in order to identify outsiders leveraging stolen credentials, insiders that are not following policies and procedures, and malicious insiders. Privileged user behavior analytics solutions help you gain insight into privileged activity with a behavioral baseline based on machine learning algorithms that consider user activity, account behavior, access behavior, credential sensitivity, and similar user behavior.
Getting the most from PAM
Managing privileged access helps organizations prevent devastating data breaches and comply with regulatory requirements. But it can be difficult for security teams that are understaffed and struggling to maintain access information across complex IT infrastructures.
By establishing comprehensive visibility into privileged accounts, enacting sound policies, implementing least privilege, investing in the right solutions, and monitoring activity, you can prevent privileged accounts from being abused and effectively tackle security risks both inside and outside your organization.
Anne Grahn contributed to this post.




